Use CaseS
Zero Trust
Complete Zero Trust with Invary
Zero Trust principles emphasize the necessity of continuously verifying trust across all components of your system, yet many implementations overlook the most foundational layers. While users and access controls often take center stage in Zero Trust architectures, critical assets and resources, such as hardware and operating system layers, are frequently left unverified.
Invary addresses this gap by extending Zero Trust principles to the foundation of your system, ensuring runtime integrity and safeguarding vital layers often ignored by traditional security solutions.
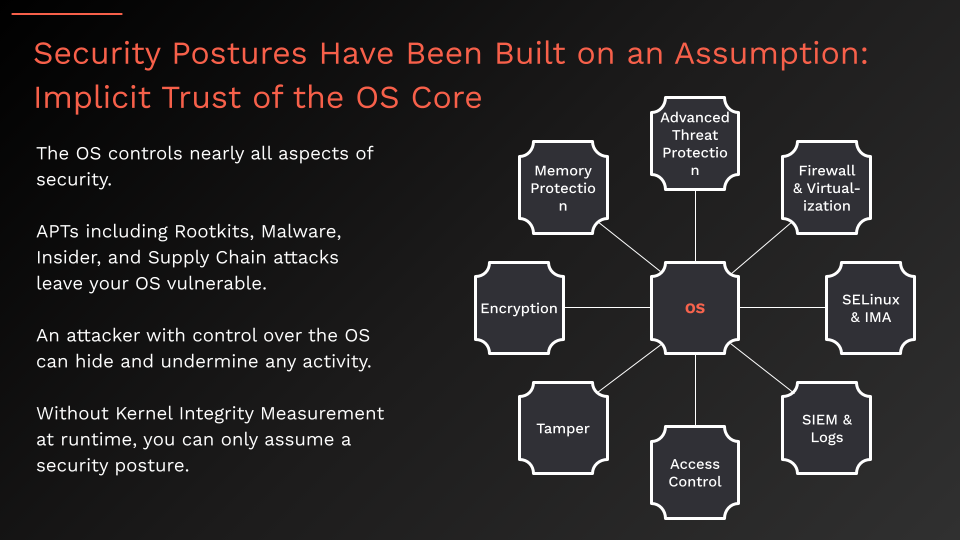
The Flaw in Assuming Foundational Trust
As illustrated in the first image, many security frameworks assume the foundational layers of a system are inherently trustworthy. Attackers exploit this oversight, leveraging rootkits, supply chain vulnerabilities, and insider threats to undermine these critical components.
Without Runtime Integrity measurement, organizations are left to assume their security posture is intact, introducing unnecessary risk. Invary eliminates this assumption by continuously verifying that the behavior of these vital layers aligns with established baselines, ensuring a secure and resilient foundation.
Extending Zero Trust to Foundational Layers
Zero Trust models traditionally focus on users, assets, and resources. However, the broader definition of "assets" often overlooks foundational system components that mediate all interactions. A compromised foundation can negate the effectiveness of even the most robust access control measures, allowing attackers to operate undetected.
Invary extends Zero Trust principles to include these core elements, ensuring that the entire system—from assets to resources—remains protected and verifiable.
Real-Time Runtime Integrity Validation
Invary's Runtime Integrity platform is designed to continuously validate the foundational layers of your system in real-time. By leveraging advanced Integrity Measurement technology licensed from the NSA, Invary ensures that these vital layers adhere to trusted baselines, detecting any deviations that could signal a compromise.
This approach aligns seamlessly with Zero Trust’s "never trust, always verify" principle, offering real-time assurance that all critical components remain secure.
Transforming Zero Trust into a Comprehensive Strategy
With Invary, Zero Trust architectures are elevated to encompass not just users and access controls but the very foundation upon which your systems operate. By addressing this critical gap, Invary empowers organizations to implement Zero Trust principles holistically, reducing risk and ensuring that every layer of their systems remains resilient in the face of evolving threats.
This innovation transforms Zero Trust from a concept to a comprehensive security strategy, protecting both the surface and the core of your infrastructure.
Zero Trust Webinar
Learn more and discover how to get an easy win for any Zero Trust initiative. By delivering provable trust of asset integrity at the foundational operating system level, security posture will be significantly improved while providing easy deployment, no complex infrastructure changes, and affordability.
Further Reading: Cloud Security Alliance Article
Read more in the article, "Integrity: An Overlooked Foundation of Zero Trust," from the Cloud Security Alliance.

