Use CaseS
Kernel Security
The Kernel: The Unseen Battleground for Security
In today’s evolving cyber threat environment, where attackers continuously evolve their methods, the kernel remains one of the most vulnerable and misunderstood components of system security. The kernel, the core of the operating system, arbitrates virtually all aspects of security, from process control to enforcing access permissions. Yet, despite its critical role, most modern endpoint security solutions overlook it entirely. These solutions assume the kernel is inherently trustworthy—a dangerous assumption that attackers have exploited with increasing precision.
Rootkits: Exploiting the Blind Spot

The first image illustrates a technique used by advanced rootkits: redirecting operating system calls that endpoint detection and response (EDR) or extended detection and response (XDR) solutions rely on. By hijacking key functions such as fsnotify_open, attackers can conceal malicious activity from security tools. For example, while the security software believes it is monitoring file access and exfiltration, the rootkit silently redirects these calls, leaving no trace in event logs. The result is a complete breakdown of trust between the security solution and the system it’s meant to protect. This vulnerability exposes the inherent flaw in assuming kernel integrity without verifying it in real time.
Beyond Boot-Time Protections
.png)
Many organizations rely on boot-time protections like Secure Boot and Kernel Lockdown to ensure the system starts in a trusted state. However, as shown in the second image, this trust is only valid at boot time. Once the system is running, attackers have ample opportunity to compromise the kernel in memory through rootkits, supply chain attacks, or insider threats. Without continuous runtime integrity verification, the system becomes increasingly vulnerable over time. Invary addresses this critical gap by extending the concept of integrity appraisal from boot to runtime, ensuring the kernel remains in a verified state throughout the lifecycle of the system. This approach eliminates the blind spots that traditional solutions leave unprotected.
The Kernel: The Foundation of Your Security Posture
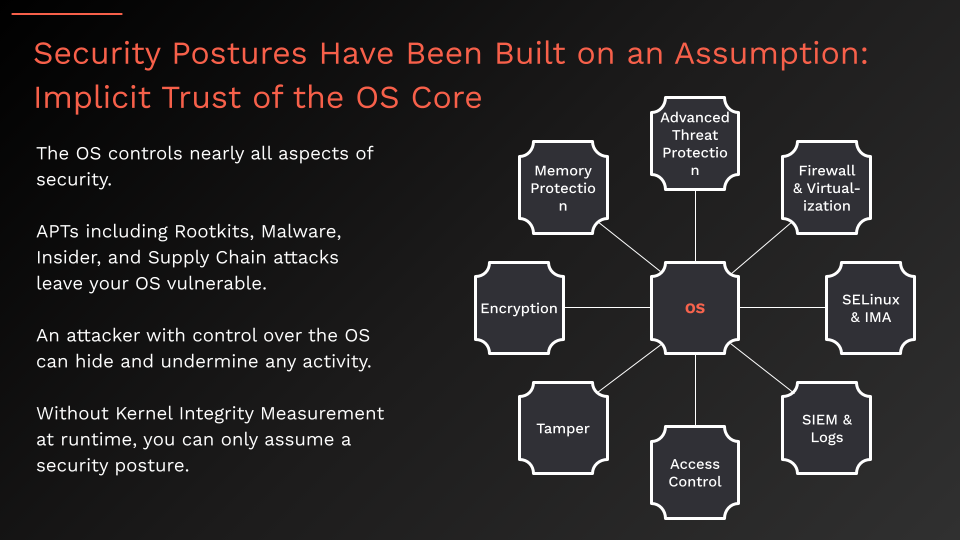
The third image underscores the kernel’s role as the centerpiece of your security posture. From encryption to access control, every security mechanism ultimately relies on the kernel to function properly. However, without a runtime kernel integrity solution like Invary, this trust is merely an assumption. A compromised kernel undermines every security tool and protocol, rendering even the most advanced defenses ineffective. Attackers with control over the kernel can disable logging, bypass access controls, and tamper with data—all while remaining undetected.
Why Invary is Essential
Invary’s Runtime Integrity kernel verification redefines endpoint security by addressing the root of the problem: the kernel itself. By continuously monitoring and verifying kernel operations at runtime, Invary eliminates the assumptions upon which modern security stacks are built. It ensures that the foundation of your security posture remains intact, preventing attackers from exploiting the very system meant to defend against them.
In today’s high-stakes cyber landscape, safeguarding the kernel is essential for maintaining system integrity and security. Invary’s approach provides the assurance that your systems are operating as intended, securing the core of your infrastructure and fortifying your defenses against the most sophisticated threats.

